Should you change the default user rights assignments in Windows 10? That’s the question. If you ask my college the AD expert, he will tell you to run away and don’t even think about changing the defaults. (He will back it up with some pretty funny stories as well about who someone did it and locked out a company and maybe even a ship)
If you ask the Security team, the answer is a yes. We should set them.
Let taks a look. We will start at my favourite site. The Windows 2004 security baseline. MS recommend quite a few setting to be applied. When we add another baseline from the Security team we end up with the table below.
| Policy Setting Name | Windows 10 |
|---|---|
| Access Credential Manager as a trusted caller | No One (Blank) |
| Access this computer from the network | Administrators; Remote Desktop Users |
| Act as part of the operating system | No One (Blank) |
| Allow log on locally | Administrators; Users |
| Back up files and directories | Administrators |
| Create a pagefile | Administrators |
| Create a token object | No One (Blank) |
| Create global objects | Administrators; LOCAL SERVICE; NETWORK SERVICE; SERVICE |
| Create permanent shared objects | No One (Blank) |
| Debug programs | Administrators |
| Deny access to this computer from the network | NT AUTHORITY\Local Account |
| Deny log on through Remote Desktop Services | NT AUTHORITY\Local Account |
| Enable computer and user accounts to be trusted for delegation | No One (blank) |
| Force shutdown from a remote system | Administrators |
| Impersonate a client after authentication | Administrators, SERVICE, Local Service, Network Service |
| Load and unload device drivers | Administrators |
| Lock pages in memory | No One (blank) |
| Manage auditing and security log | Administrators |
| Modify firmware environment values | Administrators |
| Perform volume maintenance tasks | Administrators |
| Profile single process | Administrators |
| Restore files and directories | Administrators |
| Take ownership of files or other objects | Administrators |
First things first. Let’s check the CSP and see what we need to do. To note, you can user the nice name for the account. (i.e Administrators). But we have ever lanuguage under the sun. So we need a better way to define the accounts. Lets check the Well know SID Structures for what we need.
Lets start with the local administrator. When you check for the SID, be sure to look for the BUILTIN groups and not the domain Groups. Looking at the table the SID is S-1-5-32-544.
Now we check the local account and we get S-1-5-113.
| Account | SID |
|---|---|
| Administrators | S-1-5-32-544. |
| Local Account | S-1-5-113 |
| Local Service | S-1-5-19 |
| Network Service | S-1-5-20 |
| Service | S-1-5-6 |
So Lets set up a polcy. Lets open Endpoint Mananger.
Goto Devices -> Configuration Profiles. Select Add new.
Select “Windows 10 and Later” and Custom in the profile
Let’s enter in a Logical name. “Windows 10 User Rights Assignment” and select Save.
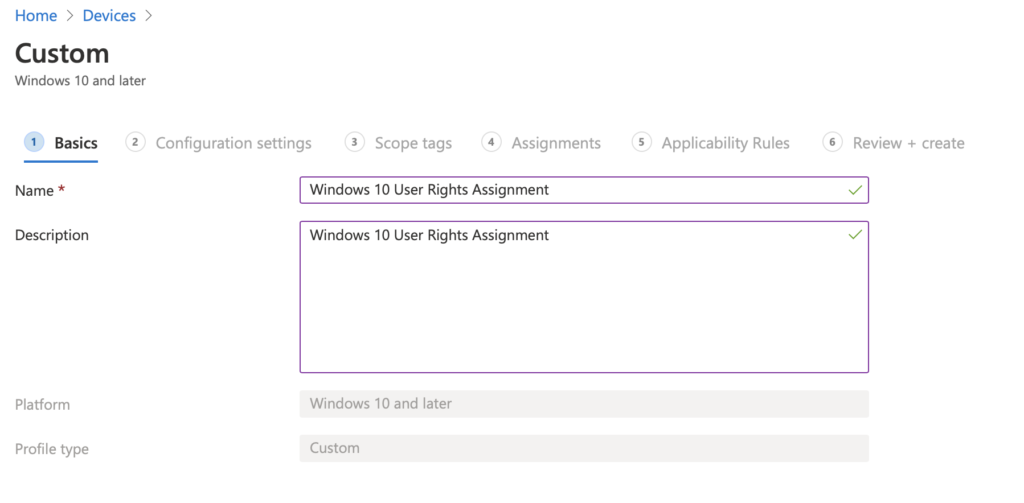
Lets Start with “Load and unload device drivers.” Select Add on the next Page. Enter in the name for the setting. I am preceding the name with URA (for User Rights Assignment). In the OMA-URI after in ./Device/Vendor/MSFT/Policy/Config/UserRights/LoadUnloadDeviceDrivers The Data Type should be string. Andter in the desired SID for the setting. In this case it will be *S-1-5-32-544. (Add the * in before to distinguish its a SID) Pres Save.
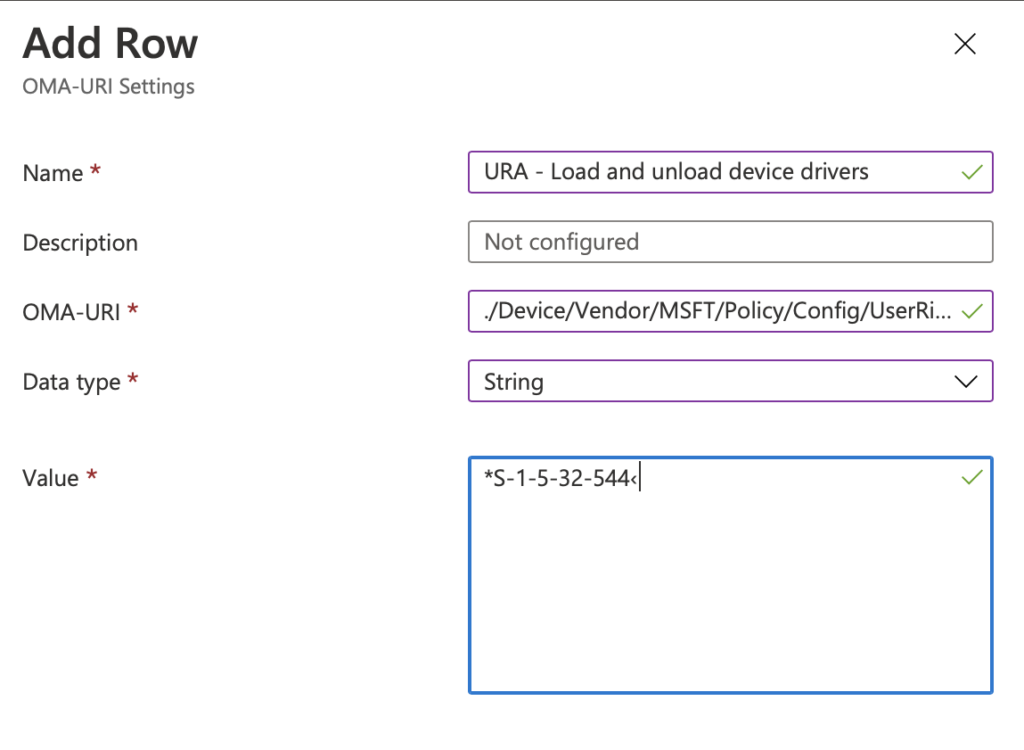
Done. What’s next. Lets go “Access Credential Manager as a trusted caller”. According the baseline no one should have access to this. But how do we define it so no one can access it. Well don’t press save with a blank field. It will fail (I learn the hard way)
Add a new one and add in the name URA – Access Credential Manager as a trusted caller. Then for the OMA-URI enter in ./Device/Vendor/MSFT/Policy/Config/UserRights/AccessCredentialManagerAsTrustedCaller. Select String again. In the data field I have set the value as </>. If you leave it black you get an error when saving it. Its really annoying if you have added 20 on and then relies they have all failed.
Repeat until you have added them all in. Select Next, and then assign them to your test group. Sync your device, and reboot.
You should also do the testing on a test machine. Just in case you lock your self out.
| NAme | OAM-URI | Setting / SID’s |
|---|---|---|
| URA – Load and unload device drivers | ./Device/Vendor/MSFT/Policy/Config/UserRights/LoadUnloadDeviceDrivers | *S-1-5-32-544 |
| URA – Generate security audits | ./Device/Vendor/MSFT/Policy/Config/UserRights/GenerateSecurityAudits | *S-1-5-20;*S-1-5-19; |
| URA – Access this computer from the network | ./Device/Vendor/MSFT/Policy/Config/UserRights/AccessFromNetwork | *S-1-5-32-555;*S-1-5-32-544 |
| URA – Enable computer and user accounts to be trusted for delegation | ./Device/Vendor/MSFT/Policy/Config/UserRights/EnableDelegation | </> |
| URA – Access Credential Manager as a trusted caller | ./Device/Vendor/MSFT/Policy/Config/UserRights/AccessCredentialManagerAsTrustedCaller | </> |
| URA – Act as part of the operating system | ./Device/Vendor/MSFT/Policy/Config/UserRights/ActAsPartOfTheOperatingSystem | </> |
| URA – Allow log on locally | ./Device/Vendor/MSFT/Policy/Config/UserRights/AllowLocalLogOn | *S-1-5-32-545;*S-1-5-32-544 |
| URA – Back up files and directories | ./Device/Vendor/MSFT/Policy/Config/UserRights/BackupFilesAndDirectories | *S-1-5-32-544 |
| URA – Create a pagefile | ./Device/Vendor/MSFT/Policy/Config/UserRights/CreatePageFile | *S-1-5-32-544 |
| URA – Create a token object | ./Device/Vendor/MSFT/Policy/Config/UserRights/CreateToken | </> |
| URA – Create global objects | ./Device/Vendor/MSFT/Policy/Config/UserRights/CreateGlobalObjects | *S-1-5-20;*S-1-5-19;*S-1-5-6;*S-1-5-32-544 |
| URA – Create permanent shared objects | ./Device/Vendor/MSFT/Policy/Config/UserRights/CreatePermanentSharedObjects | </> |
| URA – Create symbolic links | ./Device/Vendor/MSFT/Policy/Config/UserRights/CreateSymbolicLinks | </> |
| URA – Debug programs | ./Device/Vendor/MSFT/Policy/Config/UserRights/DebugPrograms | *S-1-5-32-544 |
| URA – Deny access to this computer from the network | ./Device/Vendor/MSFT/Policy/Config/UserRights/DenyAccessFromNetwork | S-1-5-32-546 |
| URA – Deny log on as a service | ./Device/Vendor/MSFT/Policy/Config/UserRights/DenyLocalLogOn | *S-1-5-32-546 |
| URA – Deny log on through Terminal Services | ./Device/Vendor/MSFT/Policy/Config/UserRights/DenyRemoteDesktopServicesLogOn | *S-1-5-32-546 |
| URA – Force shutdown from a remote system | ./Device/Vendor/MSFT/Policy/Config/UserRights/RemoteShutdown | *S-1-5-32-544 |
| URA – Impersonate a client after authentication | ./Device/Vendor/MSFT/Policy/Config/UserRights/ImpersonateClient | *S-1-5-20;*S-1-5-19;*S-1-5-6;*S-1-5-32-544 |
| URA – Increase scheduling priority’ is set to ‘Administrators | ./Device/Vendor/MSFT/Policy/Config/UserRights/IncreaseSchedulingPriority | *S-1-5-32-544 |
| URA – Load and unload device drivers | ./Device/Vendor/MSFT/Policy/Config/UserRights/LoadUnloadDeviceDrivers | *S-1-5-32-544 |
| URA – Lock pages in memory | ./Device/Vendor/MSFT/Policy/Config/UserRights/LockMemory | </> |
| URA – Manage auditing and security log | ./Device/Vendor/MSFT/Policy/Config/UserRights/ManageAuditingAndSecurityLog | *S-1-5-32-544 |
| URA – Modify an object label | ./Device/Vendor/MSFT/Policy/Config/UserRights/ModifyObjectLabel | </> |
| URA – Modify firmware environment values | ./Device/Vendor/MSFT/Policy/Config/UserRights/ModifyFirmwareEnvironment | *S-1-5-32-544 |
| URA – Perform volume maintenance tasks | ./Device/Vendor/MSFT/Policy/Config/UserRights/ManageVolume | *S-1-5-32-544 |
| URA – Profile single process | ./Device/Vendor/MSFT/Policy/Config/UserRights/ProfileSingleProcess | *S-1-5-32-544 |
| URA – Restore files and directories | ./Device/Vendor/MSFT/Policy/Config/UserRights/RestoreFilesAndDirectories | *S-1-5-32-544 |
| URA – Take ownership of files or other objects | ./Device/Vendor/MSFT/Policy/Config/UserRights/TakeOwnership | *S-1-5-32-544 |
| URA – Change the system time | ./Device/Vendor/MSFT/Policy/Config/UserRights/ChangeSystemTime | *S-1-5-32-544;*S-1-5-6 |
How can you check the User rings assignments have worked? Lets ask Mark. He usually know these things.
Lets download AccessChk from here. https://docs.microsoft.com/en-gb/sysinternals/downloads/accesschk. It allows you to check various permissions fo r files register etc. We will use it with the -a to give us the Windows account right. Lets check SeSystemtimePrivilege or Change the System time. According to the baseline, only Admin and Local services should have this right. Lets run accesschk.exe -a SeSystemtimePrivilege
C:\Users\tim>accesschk.exe -a SeSystemtimePrivilege
Accesschk v6.13 - Reports effective permissions for securable objects
Copyright ® 2006-2020 Mark Russinovich
Sysinternals - www.sysinternals.com
SeSystemtimePrivilege (Change the system time):
BUILTIN\Administrators
NT AUTHORITY\LOCAL SERVICE
Great the values are as we expect. What about the checking all the permissions. Let’s run accesschk.exe -a * to show all the permissions.
C:\Users\tim>accesschk.exe -a *
Accesschk v6.13 - Reports effective permissions for securable objects
Copyright ® 2006-2020 Mark Russinovich
Sysinternals - www.sysinternals.com
SeCreateTokenPrivilege (Create a token object):
SeAssignPrimaryTokenPrivilege (Replace a process level token):
NT AUTHORITY\NETWORK SERVICE
NT AUTHORITY\LOCAL SERVICE
SeLockMemoryPrivilege (Lock pages in memory):
SeIncreaseQuotaPrivilege (Adjust memory quotas for a process):
BUILTIN\Administrators
NT AUTHORITY\NETWORK SERVICE
NT AUTHORITY\LOCAL SERVICE
SeMachineAccountPrivilege (Add workstations to domain):
SeTcbPrivilege (Act as part of the operating system):
SeSecurityPrivilege (Manage auditing and security log):
BUILTIN\Administrators
SeTakeOwnershipPrivilege (Take ownership of files or other objects):
BUILTIN\Administrators
SeLoadDriverPrivilege (Load and unload device drivers):
BUILTIN\Administrators
SeSystemProfilePrivilege (Profile system performance):
NT SERVICE\WdiServiceHost
BUILTIN\Administrators
SeSystemtimePrivilege (Change the system time):
BUILTIN\Administrators
NT AUTHORITY\LOCAL SERVICE
SeProfileSingleProcessPrivilege (Profile single process):
BUILTIN\Administrators
SeIncreaseBasePriorityPrivilege (Increase scheduling priority):
BUILTIN\Administrators
SeCreatePagefilePrivilege (Create a pagefile):
BUILTIN\Administrators
SeCreatePermanentPrivilege (Create permanent shared objects):
SeBackupPrivilege (Back up files and directories):
BUILTIN\Administrators
SeRestorePrivilege (Restore files and directories):
BUILTIN\Backup Operators
BUILTIN\Administrators
SeShutdownPrivilege (Shut down the system):
BUILTIN\Backup Operators
BUILTIN\Users
BUILTIN\Administrators
SeDebugPrivilege (Debug programs):
BUILTIN\Administrators
SeAuditPrivilege (Generate security audits):
NT AUTHORITY\NETWORK SERVICE
NT AUTHORITY\LOCAL SERVICE
SeSystemEnvironmentPrivilege (Modify firmware environment values):
BUILTIN\Administrators
SeChangeNotifyPrivilege (Bypass traverse checking):
BUILTIN\Backup Operators
BUILTIN\Users
BUILTIN\Administrators
NT AUTHORITY\NETWORK SERVICE
NT AUTHORITY\LOCAL SERVICE
Everyone
SeRemoteShutdownPrivilege (Force shutdown from a remote system):
BUILTIN\Administrators
SeUndockPrivilege (Remove computer from docking station):
BUILTIN\Users
BUILTIN\Administrators
SeSyncAgentPrivilege (Synchronize directory service data):
SeEnableDelegationPrivilege (Enable computer and user accounts to be trusted for delegation):
SeManageVolumePrivilege (Perform volume maintenance tasks):
BUILTIN\Administrators
SeImpersonatePrivilege (Impersonate a client after authentication):
NT AUTHORITY\SERVICE
BUILTIN\Administrators
NT AUTHORITY\NETWORK SERVICE
NT AUTHORITY\LOCAL SERVICE
SeCreateGlobalPrivilege (Create global objects):
NT AUTHORITY\SERVICE
BUILTIN\Administrators
NT AUTHORITY\NETWORK SERVICE
NT AUTHORITY\LOCAL SERVICE
SeTrustedCredManAccessPrivilege (Access Credential Manager as a trusted caller):
SeRelabelPrivilege (Modify an object label):
SeIncreaseWorkingSetPrivilege (Increase a process working set):
BUILTIN\Users
SeTimeZonePrivilege (Change the time zone):
BUILTIN\Users
BUILTIN\Administrators
NT AUTHORITY\LOCAL SERVICE
SeCreateSymbolicLinkPrivilege (Create symbolic links):
SeDelegateSessionUserImpersonatePrivilege (Obtain an impersonation token for another user in the same session):
BUILTIN\Administrators
SeBatchLogonRight:
BUILTIN\Performance Log Users
BUILTIN\Backup Operators
BUILTIN\Administrators
SeInteractiveLogonRight:
BUILTIN\Backup Operators
BUILTIN\Users
BUILTIN\Administrators
EAUKUKDH0VUMDEN\Guest
SeNetworkLogonRight:
BUILTIN\Backup Operators
BUILTIN\Users
BUILTIN\Administrators
Everyone
SeServiceLogonRight:
NT SERVICE\ALL SERVICES
SeDenyBatchLogonRight:
NT AUTHORITY\Local account and member of Administrators group
NT AUTHORITY\Local account
SeDenyInteractiveLogonRight:
BUILTIN\Guests
SeDenyNetworkLogonRight:
SeDenyServiceLogonRight:
NT AUTHORITY\Local account and member of Administrators group
NT AUTHORITY\Local account
SeRemoteInteractiveLogonRight:
BUILTIN\Remote Desktop Users
BUILTIN\Administrators
SeDenyRemoteInteractiveLogonRight:
BUILTIN\GuestsNow all the rights look good. So lets plan to roll it out and hope we don’t become a funny storey for my college